
Cryptography is used to protect information, to guarantee it's not been tampered with and a way to prove the original source of the information.
The word Cryptography comes from ancient greek. Kryptos – meaning hidden secret, and graphey meaning to write. A way to turn some readable information (plaintext) to unintelligible nonsense (ciphertext). Whilst text is used in this definition, it doesn’t need to be text and could be any information that needs to be hidden, such as images or other binary data.
In the first video on Cryptography I discuss some historical moments in cryptography, explain about the terminology, show how the Caesar Shift Cipher works, how ROT13 can be used to obfuscate punchlines on forums and how to create your own ROT13 encryption in Python.
Transcript: Introduction to Cryptography part 1 - Video Transcript
The diagram below introduces fictional characters used in cryptopgrahy explanations. Alice is the one wanting to send a protected message. Bob is the intended recipient who wants to read the messages. Eve is trying to evesdrop on the message to find out what Alice is telling Bob.
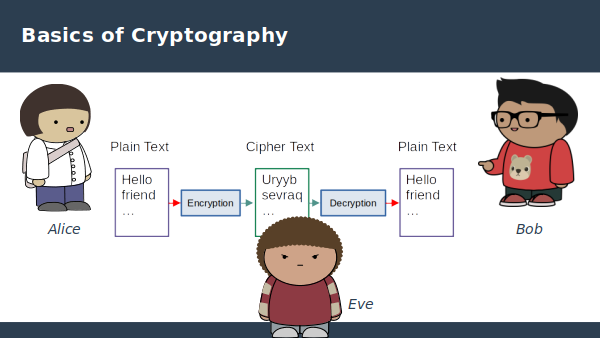
These are commonly used as fictional characters when discussing cryptography. You will often see them in other explanations and academic papers, so it makes sense to continue to use those names here.
The code below shows how you can create ROT13 encryption algorithm in Python. It's not actually needed as the Python library 'codecs' already includes an implementation of the library, but this demonstrates how it could be achieved.
while True:
print ("Please enter a string to encrypt or decrypt")
print ("or a blank string to quit")
plaintext = input()
ciphertext = ""
# If empty string exit
if (plaintext == ""):
break
for pt_chr in plaintext:
# Check if it's an alpha character (otherwise leave unchanged)
# convert to a number
pt_int = ord(pt_chr)
if (pt_int >= ord('A') and pt_int <= ord('Z')):
# it's upper case
# add 13
ct_int = pt_int + 13
# check to see if we need to wrap around
if ct_int > ord('Z'):
ct_int -= 26
ciphertext += chr(ct_int)
elif (pt_int >= ord('a') and pt_int <= ord('z')):
# it's lower case
# add 13
ct_int = pt_int + 13
# check to see if we need to wrap around
if ct_int > ord('z'):
ct_int -= 26
ciphertext += chr(ct_int)
else:
# not alpha char so just add
ciphertext += pt_chr
print ("Resulting text is:")
print (ciphertext)
print ("")
The code is only 40 lines long and some of those are comments, empty lines or print statements.
Note that this isn't necessarily the most efficient way of doing this, but it’s been broken down step by step so that you can see what happens.
I've also created a GUI application for this which is on my sister site PenguinTutor - Creating a GUI app using Guizero - ROT13 encryption.
In part two of my video I explain about how cryptography can be used to secure communications. It looks at symmetric and asymmetric key based algorithms and how they are used in different circumstances. It also covers digital signatures and how to provide the message came from who it claimed.
Transcript: Introduction to Cryptography part 2 - Video Transcript
In part three I look at Cryptographic Modes of Operation.
Transcript: Introduction to Cryptography part 3 - Video Transcript
This covers
The video explains how these are used with relevant encryption and decryption algorithms, looking at block and streaming based ciphers.
Please subscribe to Penguin Fortress on YouTube for future videos.
For more details about how security see the following guides: