
Kerberos is a popular authentication system allowing the use of third party authentication for services.

The following video explains about Kerberos ticket based authentication services, often used with Microsoft Active directory to provide a single sign-on authentication solution. It includes an explanation of the ticket granting mechanisms and session flows between the client, the kerberos key distribution centre and the server with the resources.
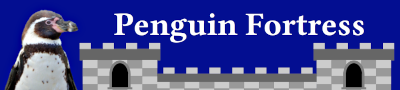
The session flow is quite complicated.
Initially the client encrypts the user's username (but not their password) using AES symmetric encryption. The username is sent to the Key Distribution Centre (KDC). Assuming the username is valid then the KDC responds with a session key which is encrypted with a hash of the users password, and a Ticket Granting Ticket (TGT) which is encrypted with the session key.
If the user has entered the valid password then that will be used to create the hash which was used for the encryption of the session key, allowing the session key to be decrypted. The client can then access the TGT and store that for future access requests.
Once the client has the TGT, then as long as it is still valid (ie. not expired) then they can use that to request a service ticket asking for access to a resource. It sends the TGT to the ticket granting service (part of the KDC) which will then return a service ticket.
The service ticket can then be sent to the server that the client would like to access along with a request for access. The resource server will check with the KDC that the ticket is valid and assuming it is will accept the client request.
This is shown in the diagram below.
Please subscribe to Penguin Fortress on YouTube for future videos.
For more details about how username and password security work on Linux systems see the following guides: